6 Actionable Cybersecurity Tips for Businesses
Last month was National Cybersecurity Awareness month. And because digital marketing will never work on a compromised website, Dave Brong, our Chief Technology Officer, shared a series of action-ready cybersecurity tips with our team to fend off digital invaders, and help us stay safe and secure online.
Here is a compilation of the things you should be keeping in mind when you’re browsing the internet:
Be Aware of Phishing Scams
In the words of my favourite Hogwarts professor, Alastor Mad-Eye Moody, “constant vigilance” is required to fight the increasing sophistication of digital invaders! Be cautious of any message you receive that contains a hyperlink, even if it’s sent from a friend or a trusted organization. Hover over the link and glance at the status bar for the actual link you’re about to click on.
When you get to a website that prompts to log in, enter the wrong password first then enter your real one – or use a password manager that matches the URL of your password to the actual site you’re on. No match = no good.
Check out this legitimate looking Apple email floating around to get iCloud access.
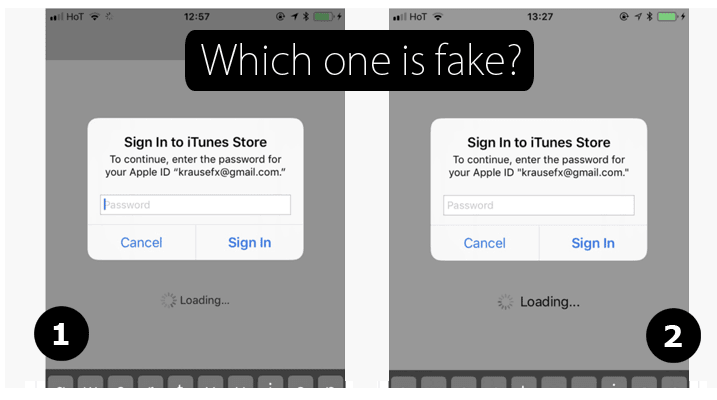
Another way to protect yourself from such clever phishing attacks is by hitting the “Home” button when it is displayed in such suspicious boxes. If hitting the button closes both the app, over which it appeared, and the dialog box disappears, then it was a phishing attack. If the dialog and the app are still there, then it is an official system dialog by Apple.
Remote Browser Isolation
Unfortunately, most organizations will at some point fall prey to phishing attacks. It just happens. What you DON’T want to happen is for that to effect your ENTIRE network (that’d be bad).
Luckily, there are ways to isolate individual web browsers on your network so that one bad apple doesn’t spoil the whole lot.
This is called “Browser isolation” or “Remote browser isolation” & like the name implies, it prevents any single compromised browser from infecting the larger network. It’s easy, affordable, non-intrusive — pretty much a no-brainer.
Lightpoint Security is a leader in remote browser isolation — schedule a demo & try it out. You’ll be happy you did.
Manage Passwords Wisely
Sometimes it feels like you’re just drowning in passwords. And it’s easy to take shortcuts like reusing the same passwords for all your accounts.
A password extension program like LastPass or 1Password (or even TeamPass) can help you manage strong, unique passwords for all of your accounts. They offer more security than using the same password throughout all of your sites. In addition, use those extensions to generate random, secure passwords and enable two-factor authentication to make it harder to break into one of your more important accounts (banks, social media, etc).
As always, change your passwords frequently. Did you know that the random American experiences at least one hacked account per year. Nothing is safe. Get used to it, it’s a way of life.
Limit Personally Identifiable Information
The more personal information you provide online, the greater the likelihood of digital invaders using that information to make you the victim of their next cyber crime. Be smart as to what personal information you put out on the internet, and just assume that at some point it will get into the wrong hands. So if you don’t need to fill out that “favorite movie while eating popcorn” profile feature, don’t.
Avoid Public Wi-Fi Networks
Digital marketing and cybersecurity work better together. Marketing is about presenting your vision to the market, and cybersecurity protects that vision from being compromised.
If you plan on working from your local Starbucks for the day, be aware that you can be making yourself an easy target for digital invaders. Public Wi-Fi connections often have shared passwords and are unsecured. If you have a mobile device with a personal hotspot option, choose this over public Wi-Fi whenever possible.
If you’re browsing on information sensitive websites, such as bank accounts and health statements, connect to them via a private computer and NEVER use public Wi-Fi. If you are using a public connection, add an extra layer of protection by using a VPN service, such as Private Internet Access.
Update Software When Prompted
Outdated software is also a huge risk for your computer as it gives cybercriminals the opportunity to take advantage of un-patched vulnerabilities and security holes.
When your computer prompts you, install all outstanding updates. In Mac, this is via the App Store. In Windows, this is via Windows Update.
You can even turn on automatic updates for your operating system and web browsers to ensure you’re always staying up-to-date. Just remember to reboot when prompted.
Lock it Up
This may seem like a no-brainer, but people sometimes put it off. Always make sure to never leave your devices unattended or unlocked as physical security carries just as much importance as technical security.
If you plan on leaving your workstation, phone, or tablet for any amount of time, make sure to lock it up. Also, lock up external storage devices like flash drives, hard drives, and discs if any sensitive information is saved on there.
—
To remain alert and to stay up-to-date on the latest cyber security risks and protocols, be sure to read our Cybersecurity Slack Channel or connect with us on Facebook, Twitter, or LinkedIn.
Need help applying the appropriate cybersecurity measures to predict and fend off digital invaders? We have a team of dedicated professionals that help businesses out-innovate digital invaders every single day. Check out our comprehensive website security solutions here or contact our team for additional information.
Most newsletters suck...
So while we technically have to call this a daily newsletter so people know what it is, it's anything but.
You won't find any 'industry standards' or 'guru best practices' here - only the real stuff that actually moves the needle.